Spider Impact can be linked to any LDAP server(s) for user authentication. This authentication is for user/password validation only. Authorization (i.e. group memberships and permissions) are still managed within the application. The application has been successfully tested with OpenLDAP and Microsoft Active Directory and should work with any LDAP server including Apache Directory Server, IBM Tivoli Directory Server, and Oracle Internet Directory.
OpenLDAP Setup
Linking Spider Impact to an OpenLDAP server simply requires knowing the Distinguished Name (DN) for the directory holding the users, and the attribute to identify the user (typically “uid” or “cn”). In order for the LDAP authentication to succeed, the user must first be entered into the Users section of the QuickScore or Scoreboard application. The username in Spider Impact must match the value of the attribute used to identify the user.
Active Directory Setup
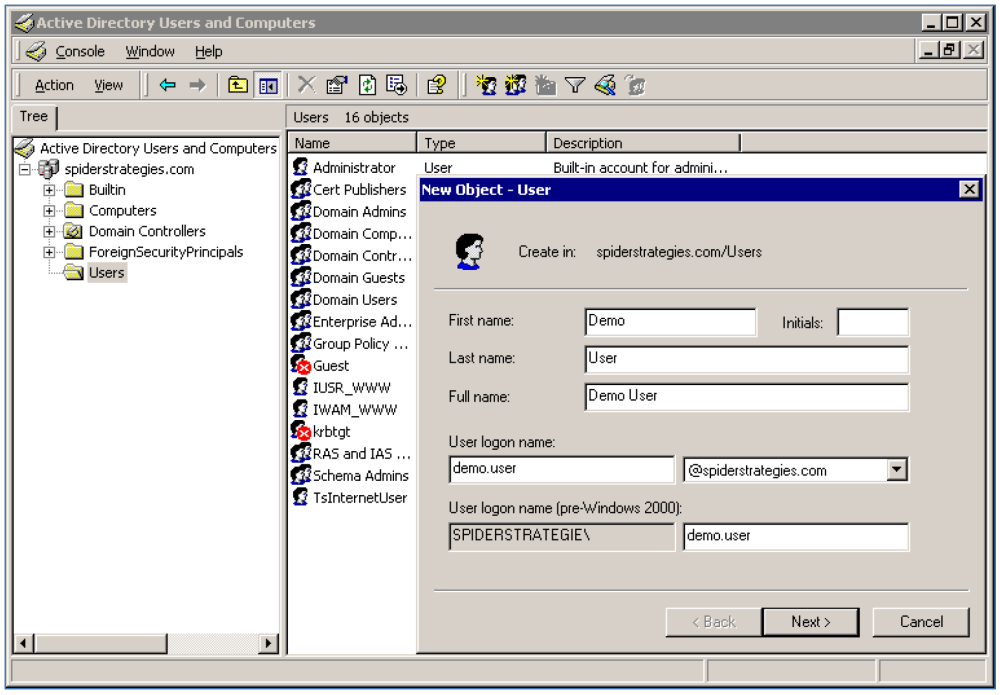
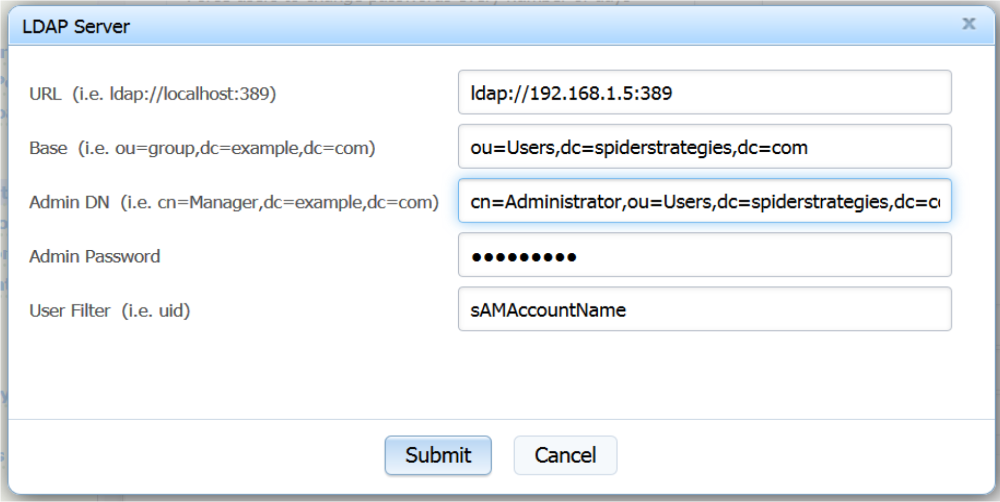
To enable LDAP authentication with Active Directory in Spider Impact, the users must be set up in a Domain Controller running Windows Server 2000, 2003, 2008, etc. The users should be part of the “Users” group and must not be set to change password at next login. For the Base, take the fully qualified domain name of the Domain Controller and the Container with the appropriate attribute labels for each level. For example, a Domain Controller “spiderstrategies.com” handling accounts in the “Users” group would be identified by separating out each element of the domain name “dc=spiderstrategies,dc=com” and adding the Container “ou=Users”, for an LDAP Base of “ou=Users,dc=spiderstrategies,dc=com”
Within the application, an administrator must first add user accounts to the software. After these initial user accounts have been added, the administrator can then enable “LDAP” authentication on the Administration > Application Administration screen. Once LDAP is enabled, a button will appear to add a connection to an LDAP server. It is possible to add multiple LDAP server connections for cases where (1) users are spread across multiple LDAP systems or (2) users are located in different Base locations within an LDAP server. Example connection settings for an Active Directory server are shown below.
User group and permission settings within Spider Impact are established within the application and are not related to LDAP group or permission settings. Integration with LDAP establishes the authentication, but authorization is handled internally. To set up groups and permissions, see the Spider Impact administration Groups section of the application.
For LDAP authentication, the user still logs in via the standard login screen. Behind the scenes, the username/password is validated against Active Directory.
Advanced Tips
For easy browsing of any LDAP Server to confirm settings, try the open source tool JXplorer available at Sourceforge